303
Cryptolocker is a term that is causing quite a stir in the IT world. But what exactly is behind it? This article sheds light on how Cryptolocker works, possible protective measures, and the effects on affected systems.
Cryptolocker: Definition and meaning
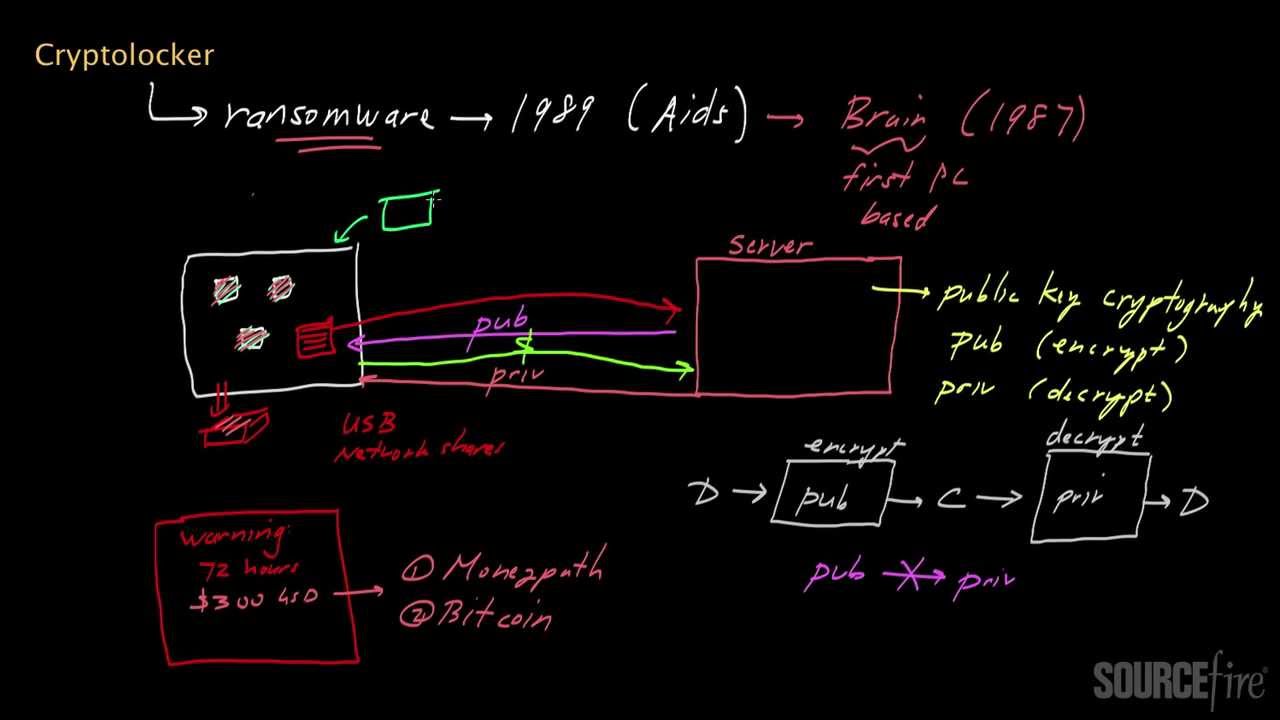
A Cryptolocker is a special form of malware, more specifically ransomware, which is used to make computer files on the infected system inaccessible by means of strong encryption and then demand a ransom from the victims in order to obtain the decryption key.
- How it works: Cryptolocker is often spread via phishing emails with malicious attachments, which are usually disguised as legitimate notifications, for example from parcel services or government agencies. After executing the malicious code, the malware begins to encrypt files on local hard drives, network drives, and sometimes even cloud storage. The affected files are encrypted using very strong algorithms (e.g., RSA with 2048 bits).
- Extortion and risks: After encryption, victims receive a message demanding payment of a ransom (usually in cryptocurrencies such as Bitcoin) in order to obtain a decryption key. If payment is not made within the deadline, the attackers threaten to destroy the key and make the data permanently inaccessible. There is no guarantee that the data will actually be released after payment.
- Significance and variants: Cryptolocker is considered the “pioneer” of modern ransomware waves, first appearing on a large scale in 2013 and causing damage worldwide. Today, there are numerous successors and variants, with the term Cryptolocker often used synonymously for all types of data-encrypting extortion malware.
- Protective measures: Typical protective measures include up-to-date backups, antivirus programs, caution when opening emails and attachments, and training in recognizing phishing attempts.
- Cryptolocker is therefore a dangerous ransomware Trojan that uses data encryption to extort ransom payments and is representative of many modern cyberattacks.
How Cryptolocker works
The way Cryptolocker works is complex and sophisticated. It uses various techniques to penetrate a system and encrypt files.
- The attack often begins with a phishing email that tricks the user into opening a malicious attachment or link. Once this happens, the ransomware is installed on the system.
- Once installed, Cryptolocker searches for specific file types and encrypts them using a strong algorithm. File types commonly affected include documents, images, and databases.
- A unique key stored on a remote server is required to decrypt the files. The attackers demand a ransom to release this key.
- Another trick used by Cryptolocker is to threaten to delete the key after a certain period of time, which increases the pressure on the victim to pay the ransom quickly.
Protect yourself from Cryptolocker: Here’s how
Protecting yourself against Cryptolocker is crucial to ensuring the integrity and availability of your data. There are various strategies you can use to minimize the risk of infection.
- Regular backups are one of the most effective ways to protect yourself against ransomware. In the event of an infection, files can be restored from a clean backup. Operating systems, software, and antivirus programs should always be kept up to date to close security gaps.
- Installing reliable antivirus software and regularly updating the operating system and all applications are crucial for closing security gaps. An up-to-date, reputable antivirus program and a firewall provide essential protection against malware and unauthorized access.
- Users should be trained in phishing attacks so that they can recognize and avoid suspicious emails and attachments. Good training can significantly reduce the likelihood of infection. Do not open any suspicious attachments or links in emails, especially if they are spam or from unknown senders. This is often how crypto viruses such as Cryptolocker are distributed.
- Implementing firewalls and other security measures can block access to malicious websites and improve network protection. Using web filters and exercising caution when surfing the web can help avoid infected websites. Public Wi-Fi networks should only be used with a VPN to prevent attacks.
- Use additional tools. Browser extensions or specialized security software can block cryptomining and other malware.
What to do if you are affected by a cryptolocker?
If you are affected by Cryptolocker (a form of ransomware), you should take the following steps:
- Immediately isolate systems and disconnect them from the network to prevent the malware from spreading further. This means unplugging network cables, disabling Wi-Fi, or taking systems offline, but do not simply shut them down in order to preserve important data for later analysis.
- Inform your IT and security team or IT experts who specialize in cyberattacks. They can limit the attack, analyze the causes, and remove the malware.
- Document the incident in detail: Which systems are affected, which error messages or files indicate the attack, and save screenshots and logs.
- Notify the authorities if personal data is affected (e.g., data protection authority) and report the attack to the police or cybercrime unit. Your own cyber insurance should also be notified.
- If necessary, check whether current and clean backups are available to restore data from them.
- Paying the ransom is generally not recommended, as there is no guarantee that the data will be decrypted and this poses further risks.
- After damage control, the IT environment should be checked for security by experts and measures to prevent future attacks should be introduced.
- In addition, you can try to recover the encrypted data with special decryption tools, if available. It is important to completely remove the ransomware from the system, e.g., with anti-malware software or in safe mode.
previous post