705
DMARC records in DNS are crucial for email security and help to effectively prevent spoofing and domain abuse. Learn how DMARC works, what advantages it offers, and what challenges can arise during implementation.
DMARC in DNS: Why it strengthens your email security
DMARC is an established protocol for increasing security in email communication. A DMARC record in DNS allows companies and organizations to protect themselves effectively.
- DMARC stands for Domain-based Message Authentication, Reporting & Conformance and is a protocol that increases email security.
- By implementing a DMARC record in DNS, you can ward off phishing attacks and protect your domain from misuse.
- A DMARC record helps verify the authenticity of your emails and ensures that they actually originate from your domain.
- Companies and organizations that use DMARC receive detailed reports on unauthorized email activity, enabling them to optimize their security measures.
Setting up a DMARC DNS record: A step-by-step guide
A DMARC record is set up in the DNS by creating a TXT record that defines policies for handling unauthenticated emails.
- First, you need to create a DNS record for DMARC that defines the policies for your domain.
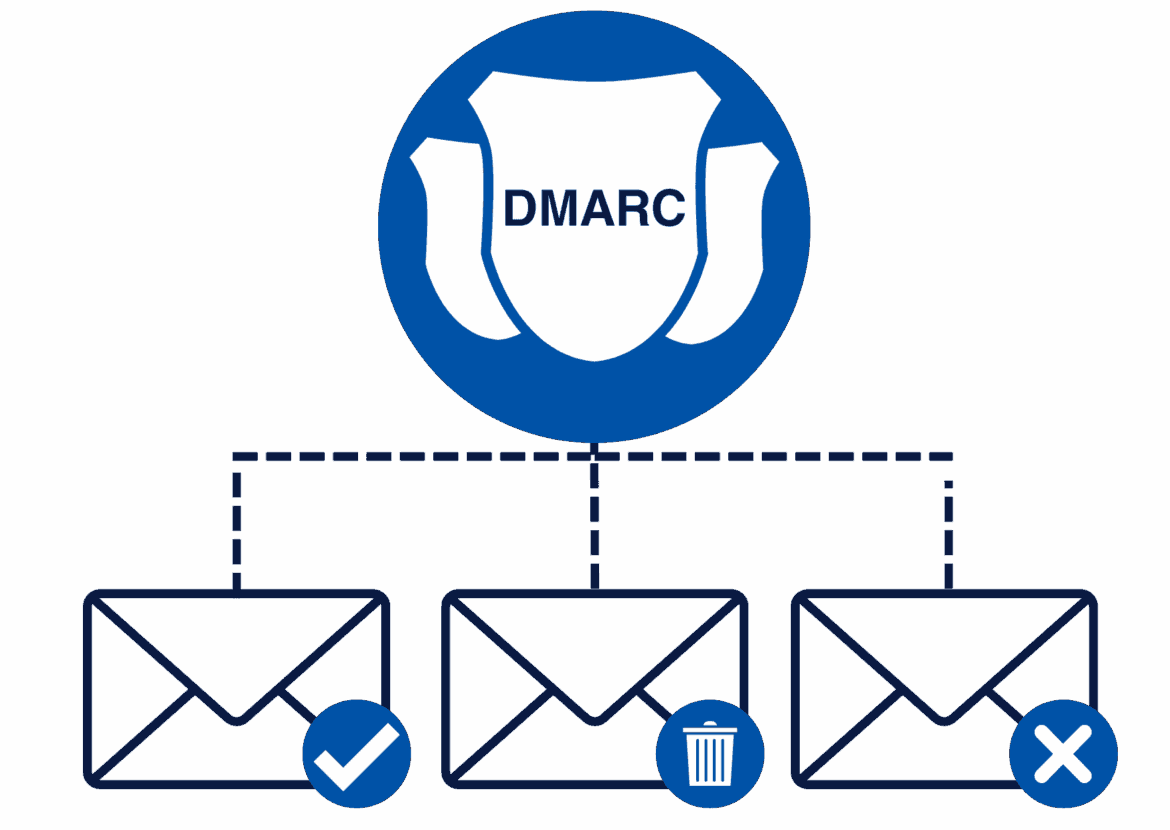
- The DMARC record contains information about how email servers should handle unauthenticated messages, such as “reject,” “quarantine,” or “none.”
- The setup requires a careful analysis of your existing SPF and DKIM records, as DMARC builds on these.
- It is advisable to test the DMARC record in “none” mode first to identify any misconfigurations before taking more restrictive measures.
Successful DMARC implementation: Tips and tricks for your domain
A structured and strategic approach is essential for the successful implementation of DMARC. There are a few key steps to keep in mind.
- Start by analyzing your current email infrastructure to identify potential vulnerabilities.
- Create a DMARC DNS record with a “none” policy to monitor the impact on your email communications.
- Regularly review DMARC reports to detect unauthorized email activity and take appropriate action.
- Once you are confident that your email communications are stable, you can change the policies to “quarantine” or “reject” to increase protection.